Marko Polo Traffer Team Blockchain Analysis
- julia05126
- Jan 16
- 8 min read

Marko Polo exposure to over $8.5M USD in illicit on-chain assets
On 17 September 2024, the Insikt Group reported on “Marko Polo,” a sophisticated Traffer Team targeting the Web3 ecosystem with cryptocurrency scams facilitated by info-stealer malware. Building on this initial research, our analysis represents the first in-depth application of blockchain forensics and asset tracing to this threat group, derived from our interactions with Marko Polo victims. This approach has uncovered how the group successfully stole over $8.5M USD between June 2024 and January 2025.
Our findings also reveal a critical element of the threat actor’s laundering methodology: funneling stolen funds into the OKX exchange. Following responsible disclosure, we engaged with the exchange, providing actionable intelligence on the laundering accounts. The exchange not only received our report but met with us to discuss the findings in detail. They have since reviewed the information and are assessing the accounts in question. We appreciate their engagement and the steps they are taking to evaluate this activity.
Read on to learn how this analysis illuminates the scale and operations of Marko Polo’s campaigns.
Who Are Marko Polo and What Is a Traffer Team?
Marko Polo operated as a Traffer Team—an organized cybercriminal group specializing in distributing malware to compromise victims and monetize the stolen data or assets. In the case of Marko Polo, their focus is on propagating info stealer malware to exfiltrate sensitive information, such as cryptocurrency wallet credentials, private keys, and session data. These teams often function within a hierarchical structure where administrators oversee operations, traffers (the operators) execute malware distribution campaigns, and specialists may handle funds extraction and laundering. This collaborative model makes traffer teams highly effective and adaptable.
Findings in the Report
The Insikt Group research consolidated disparate sets of indicators of compromise (IOCs) associated with Marko Polo’s activities. It mapped out their tactics, techniques, and procedures (TTPs) across a wide range of seemingly unrelated attack vectors, encompassing 30 unique scam types. These scams targeted Web3 users through phishing campaigns, fake applications, and other social engineering methods designed to deliver info stealer malware.
Despite the detailed analysis of their operational methods, the intelligence picture remained incomplete. Notably absent was a comprehensive understanding of the on-chain impact of Marko Polo’s exploits—specifically, the effectiveness of their attacks in draining cryptocurrency and the broader implications for the Web3 ecosystem. Understanding this on-chain footprint is critical to gauging the true scope of the threat posed by this group and their tactics.
Why the Marko Polo Traffer Team Is a Threat
Marko Polo’s operations highlighted the growing sophistication of traffer teams in targeting cryptocurrency and the Web3 space:
Scalable Operations: Their ability to launch 30 distinct scam types showcases a high degree of scalability and operational maturity.
Advanced Malware Use: By leveraging info stealers, they can efficiently drain victims’ cryptocurrency wallets.
Targeted Ecosystem: Their focus on the Web3 ecosystem aligns with the lucrative opportunities presented by its rapid growth and relatively immature security measures.
Their criminal gains have been difficult to quantify because Marko Polo typically employ strict operational security practices designed to reduce their infrastructure exposure to security analysts, they achieve this by:
Direct malware delivery to the victim via social engineering.
Their malware is only released via an “invite code” which is unique to every victim.
Marko Polo blockchain addresses are only known to the victims, they are not hard coded into the malware.
To identify the impact of the Marko Polo threat group, the intel community requires:
Access to victims who can share their blockchain addresses.
Those victims need to know which domains relate to the drain activity.
An analyst who can link the domain to one of the 30+ unique scam types operated by Marko Polo.
Because of these challenges, there is very little research into the impact of Marko Polo exploits, but we can presume they are highly effective given the volume of domains they have spun up since May 2024. With the inclusion of on-chain analytics, the community would gain a more comprehensive understanding of Marko Polo’s effectiveness, enabling a stronger response to this growing threat.
zeroShadow is uniquely positioned to help identify the scale of this threat group. We have partnerships with wallet providers, such as Phantom Wallet, giving us unique access to victims of crime, enabling us to document and analyse threats targeting their ecosystem by directly engaging with the victim, analysing the attack vector and conducting blockchain forensics.
We have recently assisted two different victims of the Marko Polo traffer team who were subjected to different attack vectors attributed to this threat actor.
Our analysis identified that the OKX deposit addresses used by Marko Polo had laundered approximately $8,170,905 USD between 29 March 2024 and 6 January 2025 via twelve OKX deposit addresses. We can directly link these deposit addresses to victims of the Marko Polo threat group.
Victim 1 - Hive-space[.]app impersonating Affine.pro (tracked as Marko Polo MP-6)
Inskit Group identified that Marko Polo was impersonating a legitimate company called affine.pro. This is a generative AI software collaboration platform that allows people to download their app and use it for free without sign-up. Virus Total (VT) has analysed the legitimate app, and it is considered safe by all security vendors on the VT platform.
In October 2024 a victim was referred to zeroShadow by the Phantom Wallet team. The victim was initially approached on X (formerly Twitter) by the @NaoliaCrypto account asking if they would be interested in testing an app.

The victim was advised to download the app from hxxps[://]hive-space[.]app/ and they were provided with an “invite code.” The invite code is an essential part of the scam, without it you cannot download the app (malware). This tactic frustrates security researchers as it typically:
Prevents download and analysis of the malware.
By failing to analyse the malware, anti virus software cannot be updated meaning new infections cannot be prevented.
If malware cannot be linked to the domain then security researchers cannot work with registrars and hosts to takedown the illicit sites.
Marko Polo has gone to the painstaking trouble of creating a legitimate brand on X which has over 16K followers and suspicious bot-like interactions accompany their 82 posts.




All of the graphics and videos are simply copied over to the HiveSpace brand from the Affine site and socials. But the telltale sign to the scam resides in the one significant difference that is a hallmark of all Marko Polo scams, the now infamous invite code (meeting ID etc).
Without this, the user is not able to download the app (malware) and this is the unusual and visible sign that you are being targeted by Marko Polo. Within the Affine app you can immediately interact with their software in the browser or download the executable file. But in the Marko Polo world, you need to be socially engineered and vetted before they will let you interact with the app (malware).


The invite code is generated by the scammer (in this case Naolia on X). Once they are certain they are interacting with a legitimate and susceptible target, they create the account on their scam domain and provide the target with an access code that will allow them to download the app (malware).
As soon as the download was performed, the infostealer malware was deployed and began to harvest all of the sensitive data stored on the victims device, including their private keys for the Phantom wallet.
HiveSpace Blockchain Analysis
The HiveSpace malware harvested all of the victims sensitive data such as passphrases and seeds for their private cryptocurrency wallets, including their Phantom wallet which stored the keys for their Solana addresses:
2YnbepiMcohhpFRGYjNewyf2CH2TsoRAm4B4LAfaZc8c
AeC8NKDJbggdJCtLWG3neUWsveu2EQLWj91zhXAo2Fon
EwCLdwUBWchdoVSdstapxS1PDQ2pnauKgCJ39tQoEWQW
On 10 October 2024 at 09:20 UTC the drain of the victims wallets commenced. We can visualise this below.

All of the victim assets were swapped to 428.2 SOL (approximately $60,571 USD) at decentralised exchanges before they were consolidated at the Marko Polo controlled address ELeTyfCtzVE1EKKFckcCmMBP1Fsw4r6cL7GDvHcntywh. From here the assets were commingled with other funds, likely stolen from other victims. These Marko Polo addresses ultimately laundered their funds primarily via six OKX deposit addresses, as well as some smaller deposits to Gate, KuCoin and Binance exchanges.
Our analysis identified that over 86% of the funds linked to the HiveSpace laundering activity was deposited into OKX, with some smaller and less frequent deposits into Gate and Binance as visualised below.

Victim 2 - Vixcall[.]live fake video conferencing (tracked as Marko Polo MP-2)
In November 2024 our latest Marko Polo victim was approached on X by a user claiming to work for cryptocurrency company Wolf Financial and was asked to appear on an associated podcast.
The victim was advised that the podcast would be conducted via a video conferencing app called Vixcall and was advised to download it from their site Vixcall[.]live. They were provided with a meeting room ID number which was needed for the download.
Once the victim had downloaded Vixcall their Phantom and Exodus wallets were drained and chat logs with the threat actor were deleted. It is believed that the threat actor accessed the victim’s X account to ensure that all chat logs were removed.
Vixcall Blockchain Analysis
After the victim downloaded the Vixcall malware, their Solana wallet was drained of all assets in just 11 minutes on 15 November 2024. The assets were drained to Marko Polo controlled address:
EXa5BLB7FEDuNLvR3EBrcgrxVn6Pd9ihNZs2X4RRkv8s.
The assets were then commingled with other Marko Polo victim funds before they were laundered via two OKX deposit addresses as depicted below.
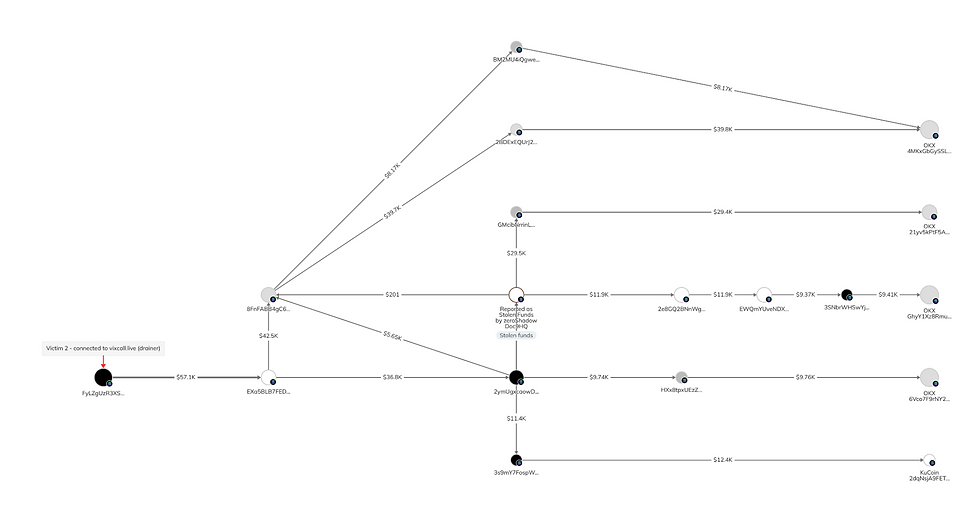
Our analysis identified that over 99% of the funds linked to the VixCall laundering activity was deposited into OKX, with a single one-off deposit to KuCoin, as visualised below.

On-chain link between Vixcall (MP-2) and HiveSpace (MP-6)
There is a clear on-chain link to show how these different scams are operated, controlled and monetised by the same single group (Marko Polo). We can see how stolen assets from the Vixcall malware were commingled with assets derived from the HiveSpace malware.

The funds converged at Solana address Doc9HQoMKFmDos5s4JdQrdjQkiJQKhh8xPPoSQTYTj35 before laundering to exchanges.
Other addresses noted in the ZachXBT research
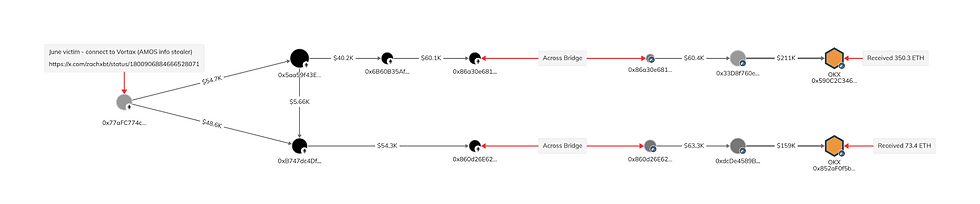
In June 2024, ZachXBT published research into a victim who had approached him for assistance. It was established that the victim had downloaded Vortax conference meeting software, this was a previous incarnation of what is now Vixcall and is tracked as Marko Polo MP-2 by Inskit Group.
Based on the details published by ZachXBT, we noted that the threat actor was using OKX back in June on the Arbitrum blockchain to launder significant amounts of stolen funds.
These OKX deposit addresses were used to launder over $1.3M USD of assets linked to the Marko Polo threat actor.
Next Steps
Based on our analysis of three Marko Polo victims, we have traced $8,525,318 in illicit funds directly tied to this threat actor’s activities. Our blockchain forensics reveal that over 95% of these stolen assets were laundered through the OKX exchange, demonstrating a systematic approach to obscuring their gains.
While this investigation provides critical insights into Marko Polo’s operations, it is highly likely that additional deposit addresses and scams associated with this group remain undiscovered. We also identified on-chain links to other cybercrime actors, including ransomware operators such as RansomHub, highlighting the broader ecosystem in which this threat actor operates.
The scale of Marko Polo’s activities in 2024 reflects the financial impact of their campaigns, stealing over $8M USD from victims worldwide. With financial gain driving continued exploitation, the threat persists. However, by targeting their laundering mechanisms and disrupting their ability to cash out, there is an opportunity to make meaningful progress in curtailing their operations.
This investigation underscores the importance of collaboration within the CTI community and with key stakeholders, including exchanges like OKX, to disrupt these actors and their ecosystems. By sharing intelligence, leveraging advanced tools like blockchain forensics, and working towards a common goal, we can make the Web3 ecosystem a more secure space. Together, we are safer.
Original article by the zeroShadow team




Comments